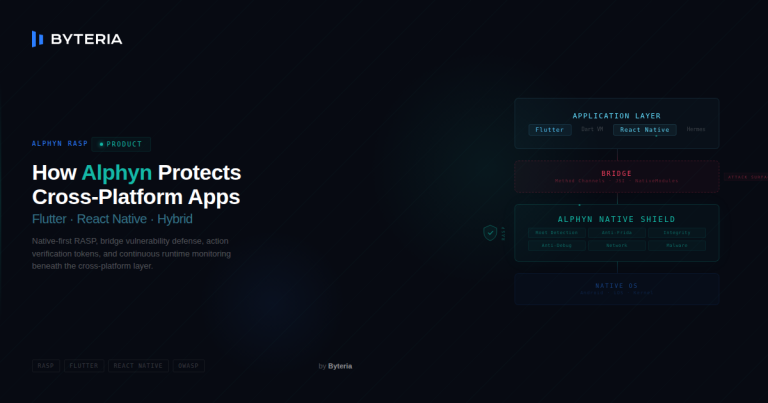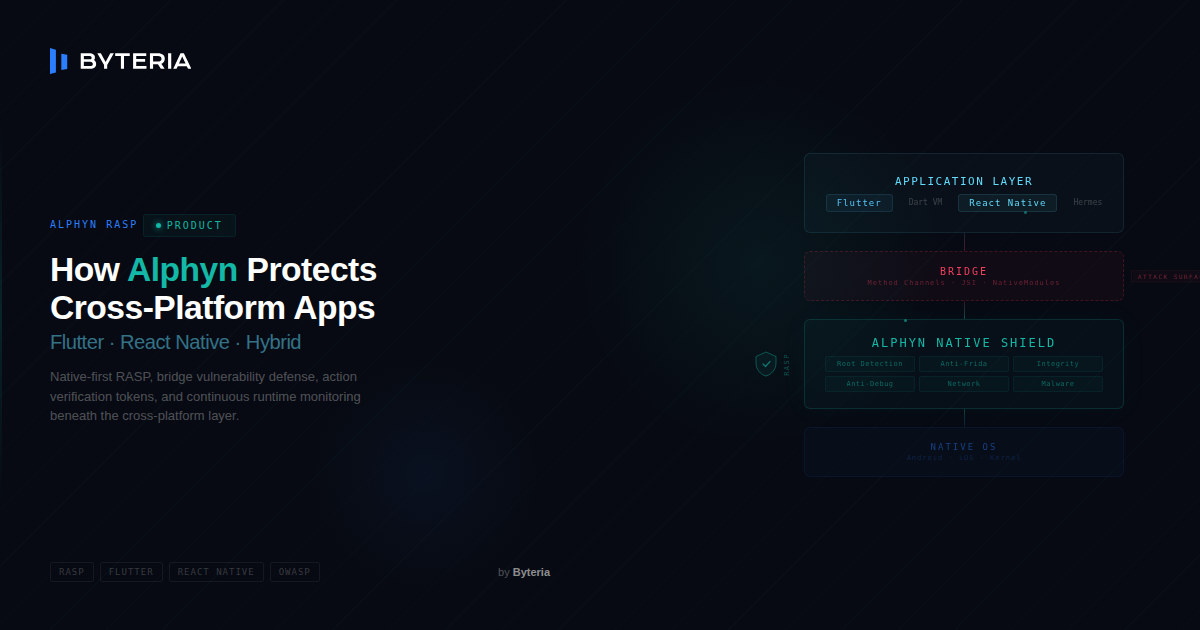
How Alphyn Protects Flutter and React Native Apps
In the rapidly evolving world of mobile development, cross-platform frameworks like Flutter and React Native have become a widely adopted choice for efficiency. They…
Read MorePosts
-
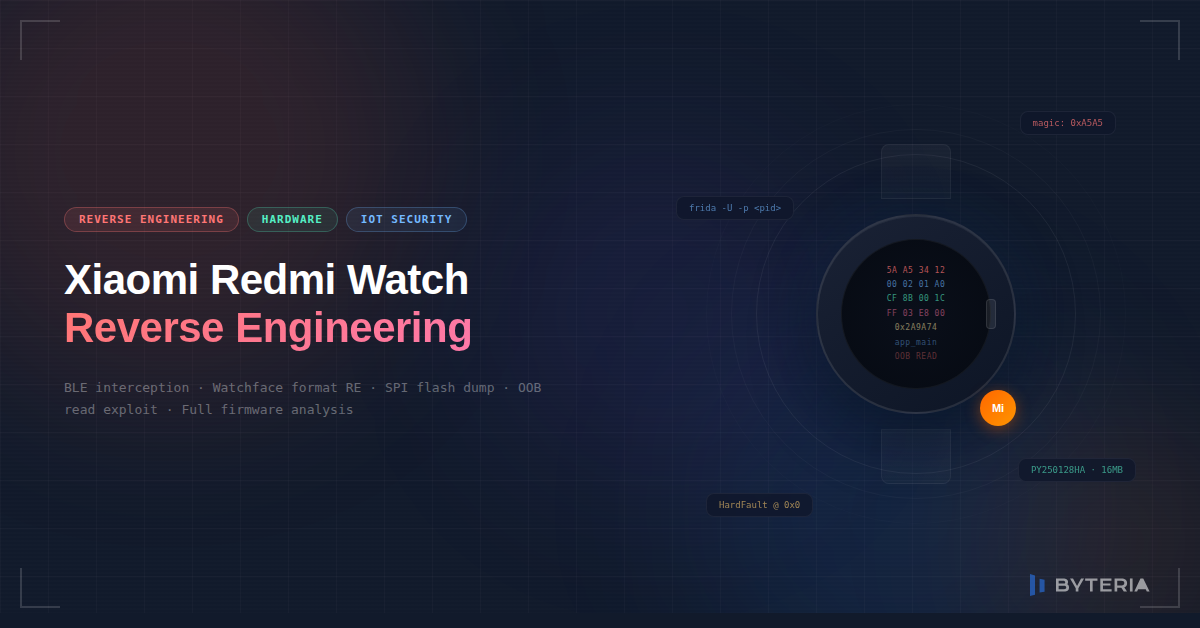
Reversing the Xiaomi Redmi Watch Through Crafted Watchfaces
How much security can you expect from a $50 smartwatch? We decided to find out. This is a full technical writeup of our research into the Xiaomi Redmi Watch 5 Active, a SiFli SF32LB551-based wearable that Xiaomi markets as running HyperOS, but under the hood it’s actually RT-Thread (a popular open-source RTOS for embedded systems).…
-
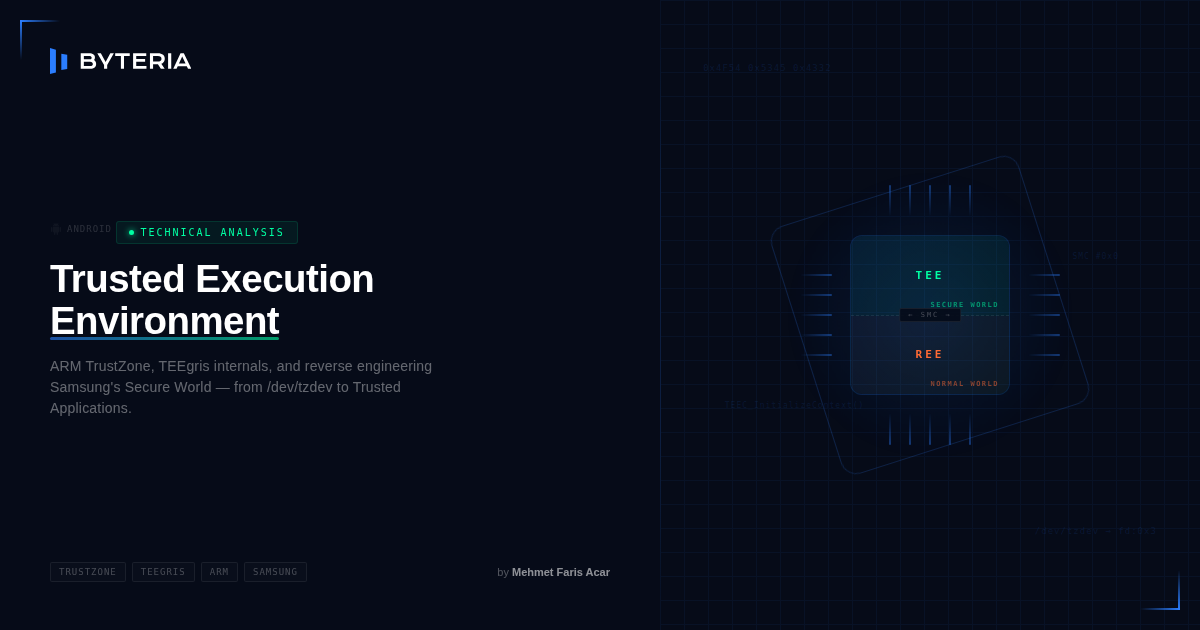
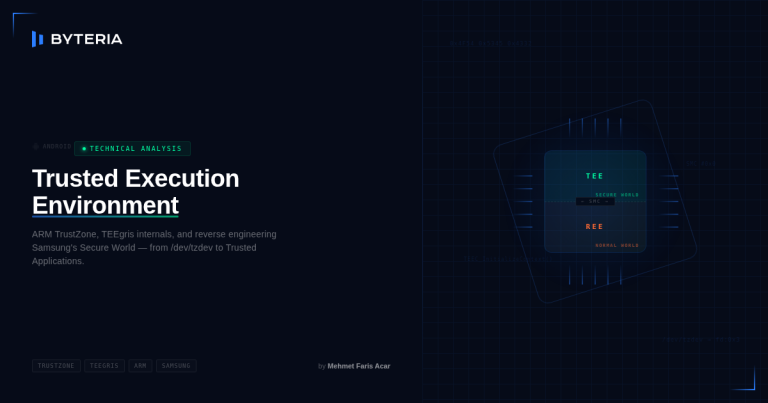
Android – Trusted Execution Environment
TEE (Trusted Execution Environment) is a general security technology used across different architectures and platforms. In this article, however, we will focus specifically on TEE solutions in Android devices. On Android devices, TEE is a hardware-backed isolated execution environment provided by the processor. The operating system and applications we use in daily life run in…
-
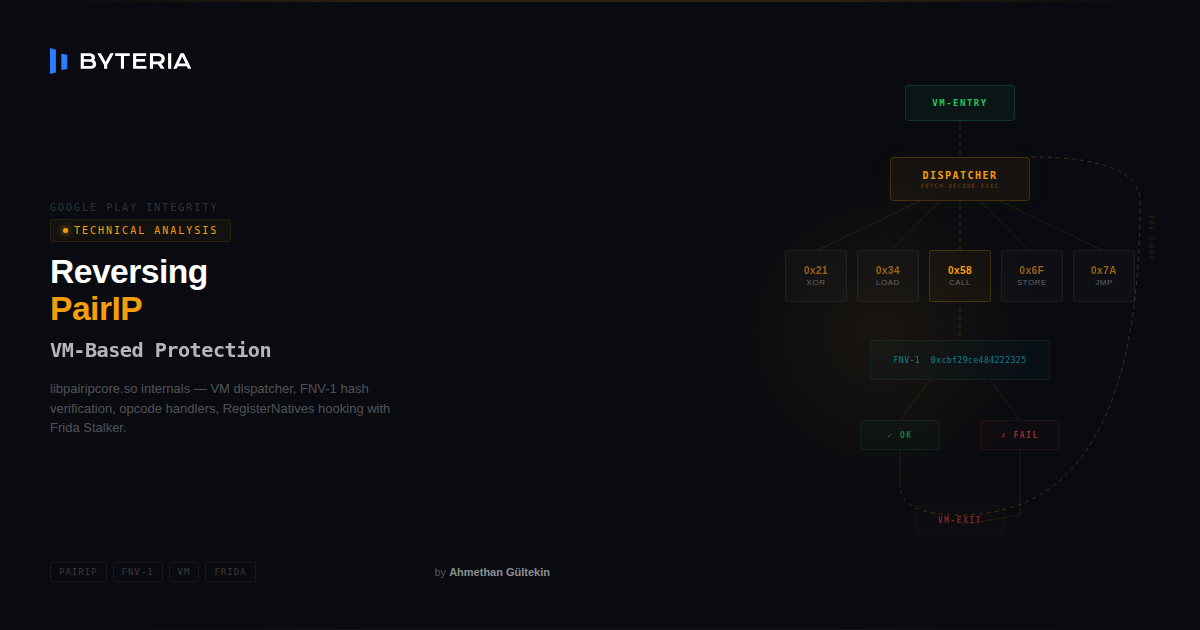
Reversing Google’s New VM-Based Integrity Protection: PairIP
Google replaced its long-standing integrity protection with the Safetynet infrastructure in 2024, with a new structure called PairIP. When you enter the Safetynet documentation page, you will see the warning “Warning: The SafetyNet Attestation API is deprecated and has been replaced by the Play Integrity API. Learn more.” So what is this PairIP? What are…
-
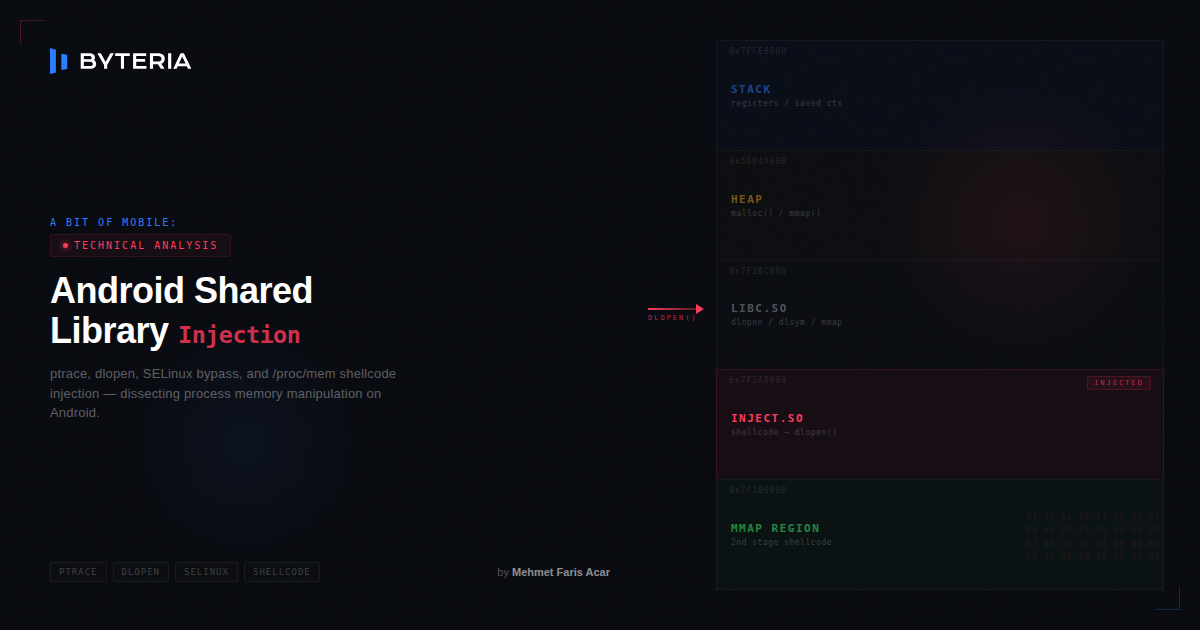
a bit of mobile: Android Shared Library Injection
Bir processin içine özel bir dinamik kütüphaneyi yükleyerek o processin davranışını değiştirmek veya manipüle etmek için kullanılan güçlü bir tekniktir. Bu işlemin en yaygın yollarından biri ptrace sistem çağrısını kullanmaktır.
-
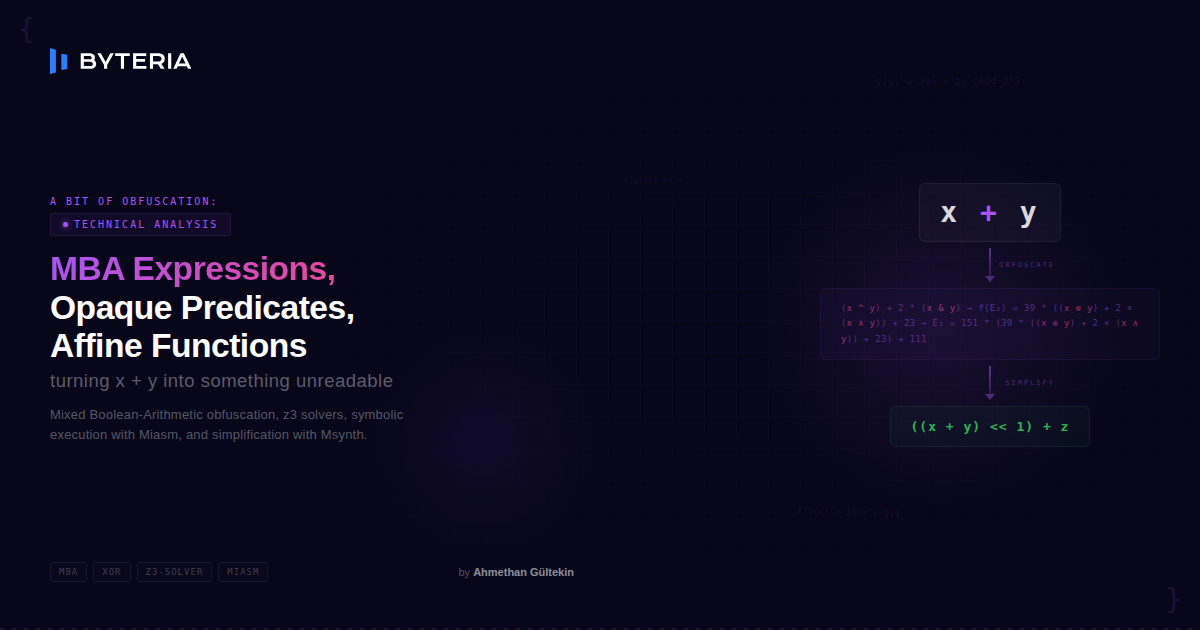
a bit of obfuscation: MBA expressions, opaque predicates, affine functions
MBA Expressions, which stands for Mixed Boolean Arithmetic, is one of the most common principles used by many obfuscators. MBA Expressions are used to confuse the data flow of the program using boolean operators, (e.g., ∧,∨,¬,⊕) and integer arithmetic operators, (e.g + (ADD) , * (IMUL) , – (DEC) ) operators.
Latest Articles
Runtime Application Self-Protection (RASP)
4 February 2026
Security Approaches in Mobile Banking Super Apps
21 January 2026
Android – Trusted Execution Environment
30 September 2025
Reach out for guest article or sponsorship opportunities
Have a question, idea, or collaboration in mind?
Feel free to reach out — we’re always open to meaningful conversations and technical discussions.