Mobile applications have become prime targets in today’s digital ecosystem. Since mobile devices store and process valuable assets such as personal data, session tokens, and financial transaction details, they represent an especially attractive target for threat actors.
However, traditional security measures provide only limited protection against the dynamics of modern threats. Today, attack vectors often bypass network and server layers and directly target the application’s runtime environment.
Such attacks can interfere with the application’s code, memory, or execution flow to disable security controls, gain unauthorized access to data, or manipulate application behavior. Therefore, an effective defense strategy should not rely solely on perimeter layers but also include mechanisms that provide real-time protection within the application’s own execution context.
This is precisely where RASP (Runtime Application Self-Protection) technology comes into play, serving as a key component of modern mobile security that enables applications to protect themselves during runtime.
How Do RASP Solutions Work?
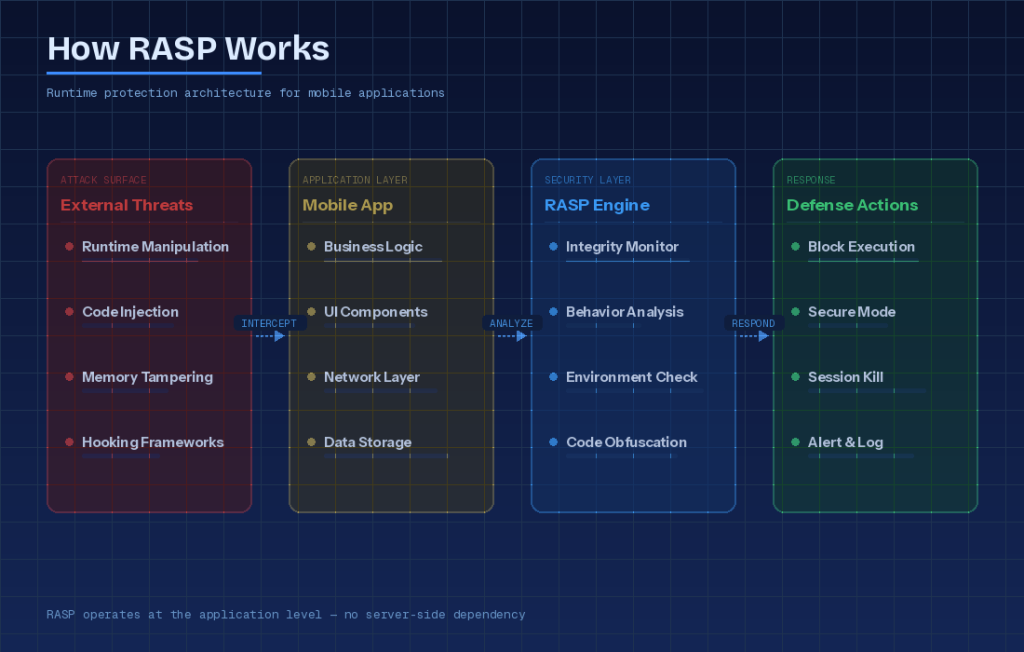
RASP solutions operate by being embedded directly into the mobile application’s runtime environment. They become active as soon as the application starts and continuously analyze both the application’s internal behavior and its operating environment. Through this analysis, RASP monitors application integrity, memory structure, and system calls to detect suspicious activities in real time.
RASP brings security controls directly into the application, enabling threat detection and response at runtime. This allows potential attacks to be identified before they occur and ensures immediate reaction when they do. For example, when malicious activities such as runtime manipulation, code injection, memory tampering, or hooking are detected, RASP activates dynamic protection mechanisms within the application. The application can switch to a secure mode, temporarily disable specific functions, or terminate the session depending on the assessed risk level.
The effectiveness of RASP solutions extends beyond runtime analysis. These technologies are also reinforced with code obfuscation techniques to enhance the application’s resilience against external interference. Obfuscation conceals the structure of the application code, making reverse engineering attempts significantly more difficult and preventing attackers from analyzing in-app security controls. In this way, RASP delivers multilayered protection at both the runtime and code levels.
In conclusion, RASP solutions preserve application integrity against rooted or jailbroken devices, dynamic analysis tools, and reverse engineering attempts, transforming the application from a passive target into an actively defending entity.
Runtime attacks represent one of the most dangerous forms of modern mobile threats. Attackers can directly manipulate application code or memory to disable security controls, hijack user sessions, or alter the application’s behavior. RASP solutions not only detect these threats but also establish a proactive defense mechanism from within the application itself.
Major Threats Prevented by RASP
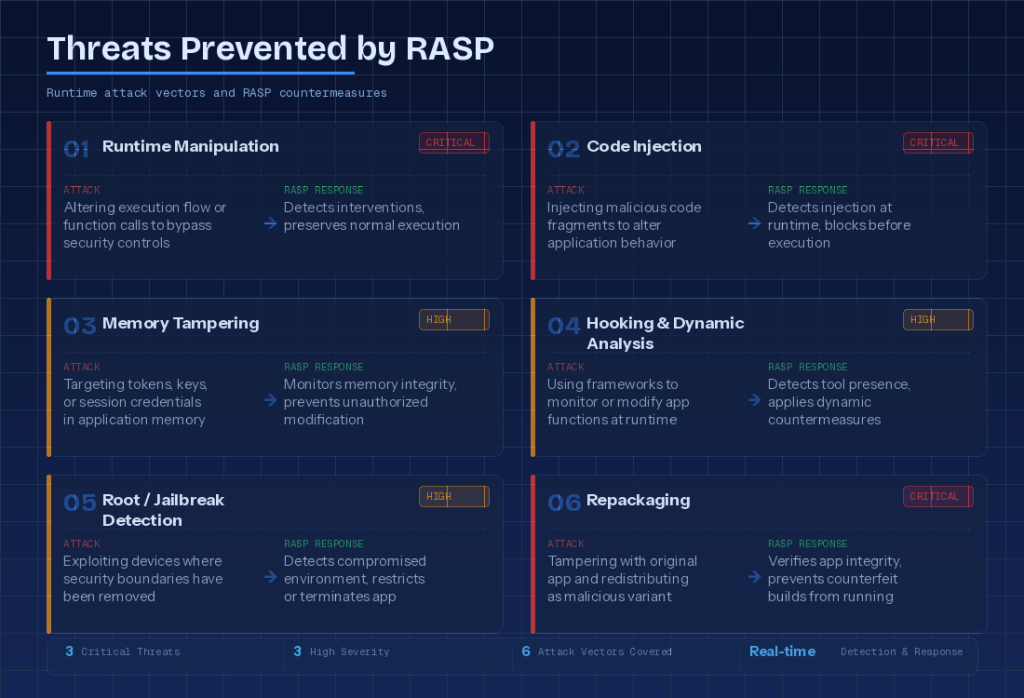
RASP solutions can detect and block a wide range of attacks that occur within the runtime environment. These threats typically aim to manipulate application behavior, disable security controls, or gain unauthorized access to sensitive data.
Below are some common attack vectors where RASP is effective:
- Runtime Manipulation: Attackers attempt to bypass security controls by altering the application’s execution flow or function calls. RASP detects such interventions and preserves the application’s normal execution.
- Code Injection: Attackers inject malicious code fragments to alter the application’s behavior. RASP detects such code injection attempts at runtime and blocks them before execution.
- Memory Tampering: Changes to an application’s memory can be used to target tokens, cryptographic keys, or session credentials. RASP monitors memory integrity and prevents such tampering.
- Hooking and Dynamic Analysis Tools: Attackers may use hooking frameworks to monitor or modify the application’s functions. RASP detects the presence of such tools and applies dynamic countermeasures to maintain the application’s security.
- Rooted and Jailbroken Environments: On devices where security boundaries have been removed, attackers can obtain system-level control. RASP detects these conditions and either restricts application access or terminate the application safely.
- Repackaging: The original application can be tampered with and redistributed as a malicious variant. RASP verifies application integrity and prevents such counterfeit builds from executing.
Conclusion
RASP protects mobile applications not only from external threats but also from attacks that occur directly within the runtime environment. This multilayered security approach, extending from the code level to the runtime phase, safeguards application integrity while ensuring the confidentiality of user data, the reliability of the application, and the long-term preservation of corporate reputation.
Built-in defense
Runtime threats require runtime protection.
Alphyn is a powerful SDK that defends against reverse engineering, tampering, and runtime attacks—all with effortless integration and enterprise-grade security.
